Email authentication is like a unique stamp on an email that proves it’s from who it says it’s from.
Think of it as a security check for your emails. This is super important because sometimes bad guys try to trick us by sending emails that look real but aren’t. Email authentication helps us trust the emails we get and makes sure they’re safe to open. So, it’s like having a trustworthy friend vouch for the email before you decide to open it.

What is Email Authentication?
Email authentication is a set of techniques and standards used to verify the legitimacy of an email message. Besides, it ensures that the sender’s identity can be validated and the message is not tampered during transit. Basically, it helps distinguish genuine emails from fraudulent ones.
Evolution of Email Authentication Standards:
The need for email authentication arose due to email scams and phishing attacks. SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) were introduced initially to ensure email authenticity, detect sender addresses, and maintain integrity. DMARC (Domain-based Message Authentication, Reporting, and Conformance) provided additional policies and reporting capabilities, reducing email fraud and phishing risks as threats evolve.
The Significance of Email Authentication
Email authentication plays a crucial role in securing your online communication. Hence, verifying email senders’ authenticity and preventing malicious activities ensures a safer and more reliable email experience.
Combatting Email Spoofing
An attacker can forge email headers to make it seem as if they’re coming from a legitimate source in an email spoofing tactic. This can trick recipients into revealing sensitive information or taking harmful actions. So, email authentication protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) help combat email spoofing by allowing email servers to verify the sender’s identity. SPF authorizes which servers can send emails on behalf of a domain, DKIM adds a digital signature to verify the message’s integrity, and DMARC provides policies to handle unauthenticated emails, reducing the likelihood of successful spoofing attempts.
Curbing Phishing Attacks
Phishing attacks are a common threat where attackers impersonate trusted entities to deceive recipients into disclosing personal information or installing malware. so, email authentication is pivotal in curbing phishing, making it harder for attackers to impersonate legitimate senders. By implementing authentication protocols, organizations can ensure their emails are more trustworthy, making it easier for recipients to distinguish between genuine communications and phishing attempts. So, this helps protect individuals and businesses from falling victim to fraudulent schemes and safeguard sensitive data.
Enhancing Email Deliverability
Email deliverability refers to the ability of an email to reach its intended recipient’s inbox successfully. With inadequate email authentication practices, deliverability can be negatively affected, resulting in emails being labeled as spam or failing to reach the intended recipients. By adequately configuring authentication protocols, organizations can improve their email deliverability rates. Basically , authenticating emails enhances their reputation with internet service providers (ISPs) and email providers, increasing the likelihood of successful delivery. So, this ensures that essential communications promptly reach recipients’ inboxes, improving communication effectiveness.
Core Components of Email Authentication
SPF (Sender Policy Framework):
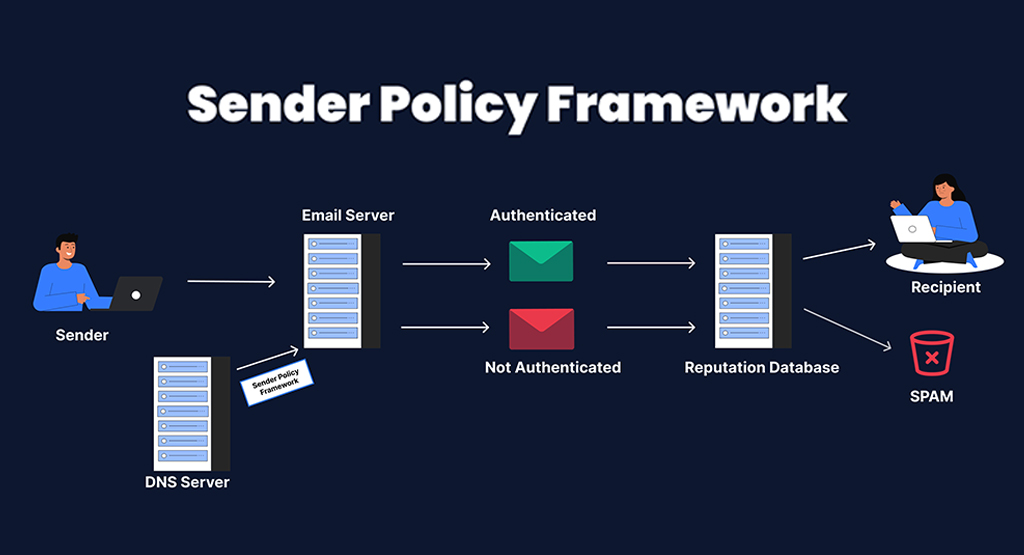
SPF is a crucial aspect of email authentication that tackles the problem of email spoofing. Spoofing occurs when a malicious sender forges the sender’s address to appear as if it’s coming from a legitimate source. So, domain owners can publish a policy in their DNS records, specifying which IP addresses are authorized to send emails on their behalf, through SPF.
When the sender’s mail server sends an email, the recipient’s mail server checks its SPF record for the sender’s domain to confirm if the originating IP address is authorized. If the IP address matches the one in the SPF record, the email passes authentication. Otherwise, it is flagged as suspicious or rejected altogether. This helps prevent unauthorized parties from impersonating legitimate senders, thus reducing the risk of phishing and other malicious activities.
DKIM (DomainKeys Identified Mail):
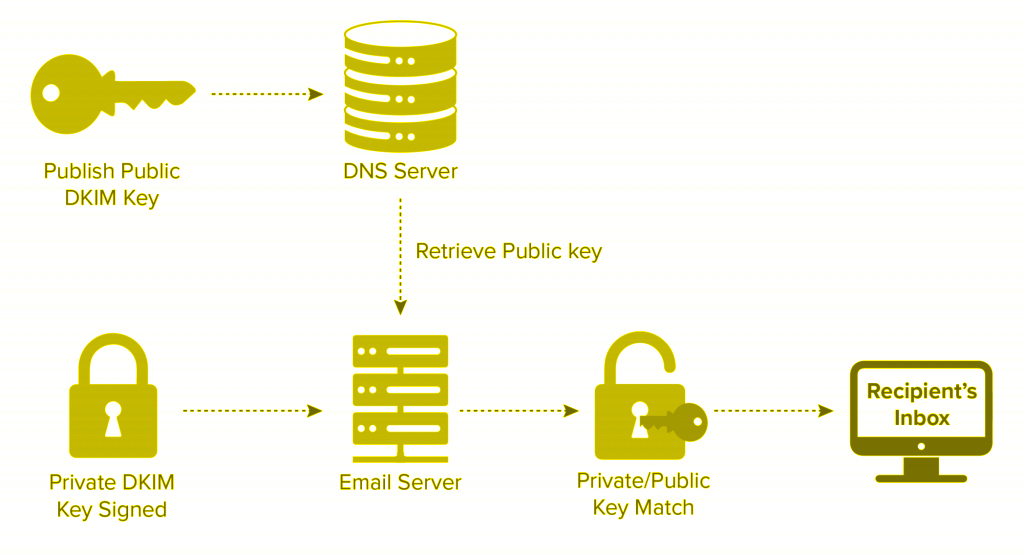
DKIM is another crucial mechanism in email authentication that focuses on ensuring the integrity of email content and confirming its origin. It works by adding a digital signature to outgoing emails. This signature is generated using cryptographic techniques and is based on the content of the email and the sender’s domain. The signature is then included in the email’s header. Upon receipt, the recipient’s mail server retrieves the public key associated with the sender’s domain from DNS and uses it to decrypt and validate the signature. If the signature is valid, it confirms that the email has not been tampered with in transit and originated from the stated domain. Basically, this helps prevent message alteration and assures recipients about the email’s authenticity.
DMARC (Domain-based Message Authentication, Reporting, and Conformance):
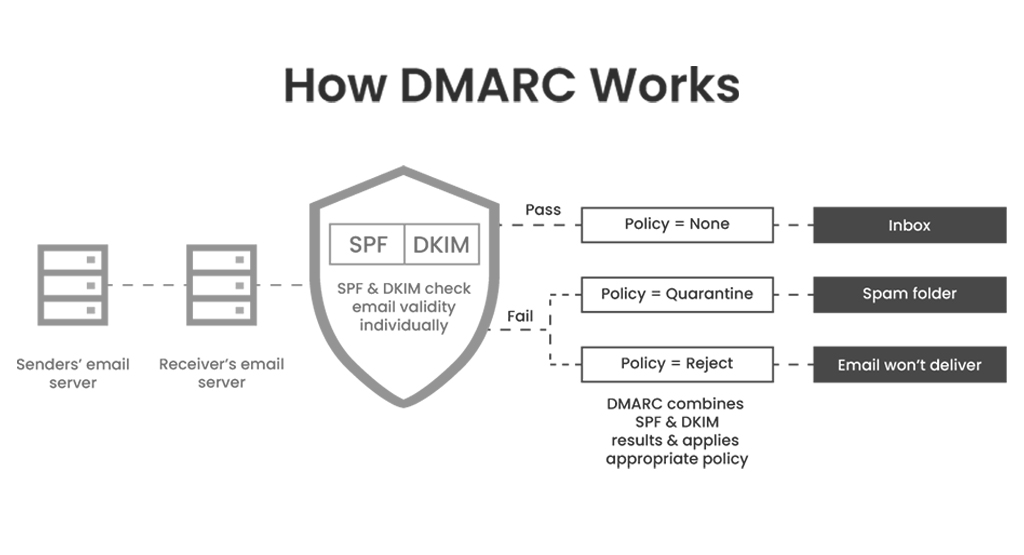
DMARC is a comprehensive framework that builds upon SPF and DKIM to give domain owners greater control and visibility over email authentication practices. It allows domain owners to publish policies specifying what actions to take for emails that fail SPF or DKIM checks. These actions can include quarantining the email, rejecting it outright, or delivering it as usual. Additionally, DMARC includes reporting mechanisms that enable domain owners to receive feedback on email authentication results. This feedback includes information about which emails passed or failed authentication, providing valuable insights into potential unauthorized use of their domains. So, by implementing DMARC, organizations can enforce strict email authentication policies, mitigate the risk of domain abuse, and enhance trust in their email communications.
SPF (Sender Policy Framework)
What is SPF? What is the purpose of SPF?
SPF, or Sender Policy Framework, is a vital tool in email authentication. Its primary purpose is to prevent email spoofing, a common tactic used by spammers and cybercriminals to impersonate legitimate senders and deceive recipients. Basically, by implementing SPF, organizations can specify which IP addresses are authorized to send emails on behalf of their domain, thereby reducing the risk of fraudulent emails reaching recipients.
How SPF Works
SPF operates by adding a particular DNS record to a domain’s DNS settings. This record contains a list of IP addresses permitted to send emails claiming to be from that domain. When an email is received, the recipient’s server checks the SPF record of the sender’s domain to verify if the sending IP is authorized. If the IP matches the one listed in the SPF record, the email passes authentication; otherwise, it may be marked as spam or rejected.
Implementing SPF Records
Implementing SPF records involves accessing the domain’s DNS settings and adding a TXT record containing the SPF information. This record typically includes directives specifying which IP addresses can email the domain. So, administrators can choose to include specific IPs, ranges, or even third-party services authorized to send emails on behalf of the domain. It is crucial to ensure that the SPF record is accurately configured in order to avoid unintended consequences, such as legitimate emails being marked as spam.
Common Pitfalls and Best Practices For SPF
Despite its effectiveness, SPF implementation can encounter several pitfalls if not managed correctly. Common issues include incomplete SPF records, misconfigured DNS settings, and failure to update records as infrastructure changes. To mitigate these risks, organizations should regularly review and update their SPF records to reflect changes in their email infrastructure. Furthermore, organizations must monitor SPF authentication failures and adjust policies accordingly to prevent legitimate emails from being blocked.
DKIM (DomainKeys Identified Mail)
What is DKIM?
DKIM signatures are like digital fingerprints for emails. The sender’s email server adds them to verify the message’s authenticity. These signatures contain cryptographic keys that help recipients ensure the email hasn’t been tampered with during transit.So, by validating DKIM signatures, recipients can trust that the email comes from the claimed sender.
DKIM Key Generation Process
Generating DKIM keys involves creating a pair of private and public cryptographic keys. The sender’s email server keeps the private key securely, while the public key is published in the sender’s DNS records. When an email is sent, the sender’s server signs it using the private key, and the recipient’s server verifies it using the public key fetched from DNS.
Integrating DKIM with Email Servers
Integrating DKIM with email servers typically involves configuring the software to generate DKIM signatures for outgoing emails. Moreover, This setup involves generating DKIM keys, configuring DNS records, and enabling email servers to apply DKIM signatures. Most modern email server software supports DKIM integration and provides configuration options for seamless implementation.
Troubleshooting DKIM Issues
Despite its benefits, DKIM implementation can encounter issues. Common problems include misconfigured DNS records, mismatched DKIM keys, or errors in the signature itself. Troubleshooting DKIM issues often involves:
- Verifying DNS records.
- Ensuring key consistency between sender and recipient.
- Diagnosing errors reported by email servers or email clients.
Properly addressing DKIM issues is crucial for ensuring email deliverability and maintaining the sender’s reputation.
Understanding DKIM, its crucial generation process, integration with email servers, and troubleshooting common issues is essential for email security and authenticity. So, by implementing DKIM effectively, organizations can enhance email deliverability, protect against spoofing and phishing attacks, and foster trust with recipients.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
What is DMARC?
DMARC, which stands for Domain-based Message Authentication, Reporting, and Conformance, is a powerful tool to enhance email authentication. The framework combats email spoofing, phishing, and other fraudulent activities. Basically, it facilitates email senders in authenticating their messages and enables email receivers to verify the authenticity of incoming emails. So, the aim is to create a more secure and reliable email environment, preventing any kind of scam or deceptive email from reaching the users.
Configuring DMARC Policies
Configuring DMARC policies involves setting up specific rules and guidelines for how email servers should handle messages that fail authentication checks. This includes specifying what action to take when an email fails DMARC verification, such as rejecting, quarantining, or monitoring the message. By configuring DMARC policies, organizations can better protect their email domains from being spoofed or abused by malicious actors.
Interpreting DMARC Reports
Interpreting DMARC reports is crucial for understanding the effectiveness of your email authentication efforts. You will gain valuable insights from these reports on how your domain is being used, including information about authentication failures, sources of unauthorized emails, and compliance with your DMARC policy. Hence, organizations can identify potential security threats by analyzing these reports, fine-tuning their DMARC configurations, and improving email deliverability and security.
Advanced DMARC Strategies
In addition to the basic configuration, organizations can implement several advanced strategies to maximize the effectiveness of DMARC. These may include:
- Gradual enforcement: Gradually ramp up DMARC policies to minimize disruption to legitimate email traffic while increasing protection against fraudulent emails.
- Customized reporting: Tailoring DMARC reports to focus on specific metrics or domains of interest, allowing for more targeted analysis and action.
- Partner collaboration: Working with email service providers, vendors, and other stakeholders to align DMARC policies and share threat intelligence, further strengthening email security across the ecosystem.
- Continuous monitoring and adjustment: Regularly monitor DMARC reports and adjust policies to adapt to evolving threats and ensure ongoing effectiveness.
By leveraging these advanced strategies, organizations can enhance their email authentication practices and better defend against email-based attacks.
Read: Personalized Email: Definition, Best Practices, and Trends
Benefits of Implementing Email Authentication
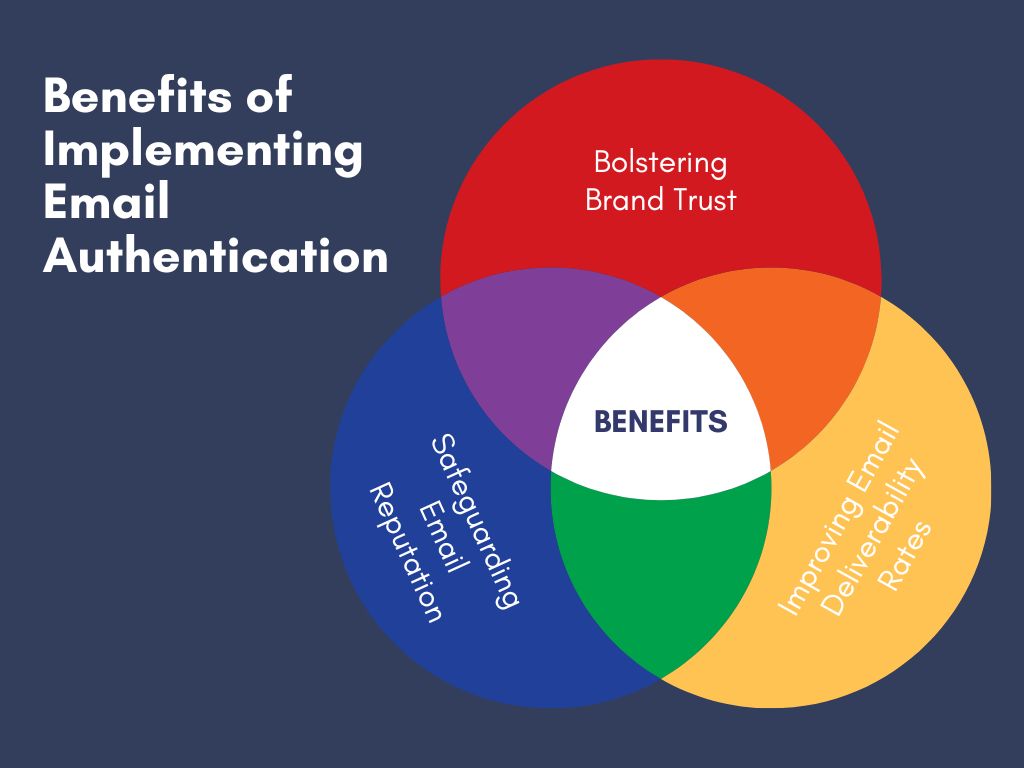
Email authentication is a crucial aspect of online communication that can significantly benefit businesses in several ways.
Bolstering Brand Trust:
Implementing email authentication measures demonstrates a commitment to security and authenticity, which can enhance brand trust among customers and stakeholders. When recipients trust the content and the sender because they see that emails are authenticated, they engage more and show greater loyalty.
Safeguarding Email Reputation:
Organizations have the capacity to shield their reputation from fraudulent activities such as phishing and spoofing by authenticating their emails. Through the use of authentication protocols like Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC), they can confirm that emails originate from legitimate sources. This reduces their risk of having their emails flagged as spam or perceived as malicious by email providers and recipients, thereby preserving their reputation.
Improving Email Deliverability Rates:
Authenticating emails improves deliverability by reducing the likelihood of email servers filtering or blocking messages. And, authenticating emails with industry-standard protocols increases the likelihood of emails arriving in intended recipients’ inboxes, reducing the chance of diversion to spam folders or outright rejection.
Email Authentication Best Practices
Email authentication is a critical aspect of maintaining the security and integrity of email communications. Let’s delve into some best practices to ensure effective email authentication:
Regularly Monitoring Email Authentication-Results:
It’s essential to regularly monitor authentication results to identify any anomalies or potential security breaches. This involves keeping a close eye on authentication mechanisms such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to ensure they are functioning correctly. By regularly monitoring authentication results, organizations can detect and mitigate unauthorized attempts to send emails on their behalf, enhancing email security.
Educating Email Users and Administrators:
Without doubt, education plays a crucial role in email authentication. It’s essential to educate email users and administrators about the significance of authentication protocols and their role in preventing email fraud and phishing attacks. Users must learn to identify suspicious emails and verify sender details before engaging with email content. On the other hand, administrators should receive comprehensive training on implementing and managing authentication protocols effectively.
Ensuring Consistent Authentication Across Domains:
Consistency is vital when it comes to email authentication across domains. Organizations need to take responsibility for ensuring all domains associated with their email infrastructure have configurations with consistent authentication mechanisms, such as SPF, DKIM, and DMARC. These actions are crucial as they maintain a unified approach towards email security and thwart any inconsistencies that malicious actors could potentially exploit. Moreover, these organizations should conduct regular audits themselves to verify that the authentication settings are consistent across all domains.
Future Trends in Email Authentication
Advancements in Email Authentication Protocols
Email authentication is transforming with continuous advancements in authentication protocols. Traditional methods are evolving to meet the growing challenges of cybersecurity. DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a notable protocol gaining prominence. DMARC boosts email security by enabling senders to dictate email authentication methods, offering a strong defense against phishing and email fraud.
Additionally, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) have become fundamental in email authentication. SPF helps verify the sender’s IP address, while DKIM adds a digital signature to emails, ensuring the integrity of the message and its source. Email authentication will become a more robust defense against malicious actors as these protocols become more widely adopted.
Integration with AI and Machine Learning
Integrating Artificial Intelligence (AI) and Machine Learning (ML) into email authentication is a game-changer. These technologies enhance the accuracy of email filtering and fraud detection. Machine learning algorithms analyze vast datasets to identify patterns and anomalies, enabling email systems to adapt and respond to evolving threats in real time.
Furthermore, by leveraging AI, email authentication systems can learn from historical data, predict potential risks, and automatically adjust security measures. This proactive approach significantly reduces the chances of false positives and negatives. It ensures that the system does not mark legitimate emails as spam, and swiftly intercepts malicious ones.
Addressing Emerging Threats
The landscape of cyber threats is ever-evolving, and email authentication must keep pace. Future trends focus on addressing emerging threats such as deepfake attacks and AI-generated phishing emails. Designers will create advanced authentication systems to detect and mitigate these sophisticated threats. These systems will protect users from deceptive tactics that could potentially compromise sensitive information.
Moreover, future email authentication solutions will likely employ behavioral analysis to assess the legitimacy of an email based on user behavior patterns. So, this approach adds an extra layer of security by considering contextual factors, making it more difficult for attackers to mimic user interactions and deceive email filters.
Read: Make Email Easier with Our Free Email Validation Checker Tool
Challenges and Limitations of Email Authentication
Compatibility Issues Across Platforms
Email authentication faces a significant hurdle in compatibility issues across various platforms. The diverse landscape of email clients and servers challenges implementing a standardized authentication system. Platforms may interpret authentication protocols differently, leading to inconsistencies and potential vulnerabilities. Achieving seamless interoperability remains a crucial concern for ensuring the effectiveness of email authentication measures.
Additionally, to address this challenge, industry stakeholders must collaborate to establish and adhere to widely accepted standards. Creating a unified framework that spans diverse platforms can enhance the compatibility of email authentication methods, fostering a more secure email ecosystem.
Overcoming Resistance to Adoption
Resistance to adopting email authentication protocols is another obstacle to fortifying the email infrastructure. Some entities may be hesitant to implement authentication measures due to concerns about the complexity of the process, potential disruptions to existing systems, or the perceived lack of immediate benefits. Convincing organizations to prioritize and invest in email authentication requires a concerted effort to communicate the long-term advantages and dispel misconceptions.
Educational initiatives and awareness campaigns play a pivotal role in overcoming resistance. By providing clear and concise information about the importance of email authentication in mitigating cyber threats, stakeholders can foster a collective understanding of its necessity. Addressing concerns and showcasing success stories can further encourage widespread adoption.
Addressing Complex Email Infrastructure
The complexity of email infrastructure poses another layer of challenges for effective authentication. With many email servers, protocols, and routing mechanisms in place, implementing authentication measures requires careful consideration of these intricacies. Failure to account for the diverse elements within email infrastructure may lead to incomplete protection against malicious activities.
And, to navigate this complexity, a holistic approach is essential. The design of email authentication solutions should accommodate email environments. Standardizing practices across the industry while allowing for customization based on specific organizational needs can contribute to developing robust authentication systems that seamlessly integrate with complex email infrastructures.
Conclusion
In conclusion, email authentication is vital for securing online communications. So, by implementing SPF, DKIM, and DMARC protocols, organizations can prevent spoofing, phishing, and other malicious activities, thus safeguarding sensitive information and maintaining trust with recipients.
FAQs about Email Authentication
What is Email Authentication, and why is it essential?
Email Authentication is a set of techniques and protocols that verify the legitimacy of an email sender. It is essential to prevent email spoofing, phishing, and unauthorized use of a domain. It enhances email security and trustworthiness.
How do SPF, DKIM, and DMARC work together?
SPF (Sender Policy Framework) verifies the sender’s IP address, DKIM (DomainKeys Identified Mail) authenticates the email’s content, and DMARC (Domain-based Message Authentication, Reporting, and Conformance) combines SPF and DKIM, providing a comprehensive authentication and reporting framework to prevent email abuse.
What are some common challenges in implementing Email Authentication?
Common challenges include misconfigurations, understanding and configuring the different authentication protocols (SPF, DKIM, DMARC), dealing with third-party services, and managing the potential impact on legitimate email delivery.
How can small businesses benefit from Email Authentication?
Small businesses build trust, minimize phishing attack risks, and ensure the delivery of their emails to recipients’ inboxes for their benefit. Email Authentication helps build credibility and protects the business and its customers from malicious activities.
How often should you review and update Email Authentication?
You should regularly conduct reviews, especially when email infrastructure or services change. Quarterly assessments make a good starting point, but promptly making adjustments in response to changes in the organization’s email landscape or evolving security threats is necessary.
How to authenticate an email in Gmail?
To make sure your emails in Gmail are authentic, set up SPF, DKIM, and DMARC. These tools will stop people from pretending to be you (spoofing) and keep your emails out of spam folders. SPF is a type of DNS record that says which servers can send emails for your domain. DKIM confirms the email’s genuineness with a digital signature. DMARC tells you what to do with emails that fail SPF or DKIM checks. These setups help your emails reach their destination better and avoid being marked as spam.
