SPF, DKIM, and DMARC are essential email authentication protocols. They work together to verify an email’s legitimacy, ensuring it comes from an authorized sender and hasn’t been tampered with. This trio is crucial for preventing spam and phishing and enhancing email deliverability.
The Foundation of Email Trust: Understanding SPF, DKIM, and DMARC
In today’s digital world, email is a primary communication tool for businesses and individuals alike. However, its widespread use also makes it a prime target for malicious activities like spam, phishing, and spoofing. To combat these threats, a set of robust email authentication protocols has been developed: Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC). These protocols are not just technical jargon; they are the bedrock of email trust and critical for ensuring your messages reach their intended recipients.
Why Email Authentication Matters
Imagine receiving an official-looking email from your bank asking for sensitive information. Without proper authentication, it’s difficult to know if the email is genuinely from your bank or a cleverly disguised phishing attempt. This is where SPF, DKIM, and DMARC step in. They provide a mechanism for email servers to verify the sender’s identity and the email’s integrity.
- Combating Spam: A significant portion of internet traffic is spam. Authentication helps filter out unwanted messages.
- Preventing Phishing: These protocols make it harder for attackers to impersonate legitimate organizations.
- Improving Deliverability: Emails that pass authentication checks are more likely to land in the inbox, rather than the spam folder.
- Protecting Brand Reputation: By preventing unauthorized use of your domain, you safeguard your brand’s credibility.
Sender Policy Framework (SPF): Who Can Send on My Behalf?
SPF is like a guest list for your domain. It specifies which mail servers are authorized to send emails from your domain. When an email server receives a message, it checks the sender’s IP address against the SPF record published in the sender’s Domain Name System (DNS).
How SPF Works
- Publisher’s Role: The domain owner creates an SPF record, which is a TXT record in their DNS. This record lists all IP addresses and domains authorized to send email for their domain.
- Receiver’s Role: When an email arrives, the receiving mail server extracts the sender’s domain and the IP address from which the email originated.
- Verification: The receiving server then queries the sender’s DNS for their SPF record. It compares the sending IP address to the list of authorized IPs in the SPF record.
- Policy Action: Based on the SPF record’s policy, the receiving server decides how to handle the email if it doesn’t match an authorized IP:
- Pass: The email is from an authorized sender.
- Fail: The email is definitely not from an authorized sender and should be rejected or marked as spam.
- SoftFail: The email might not be from an authorized sender; it’s a suspicious but not definitive failure.
- Neutral: The sender’s SPF record doesn’t state whether the IP is authorized.
Key Aspects of SPF
- DNS TXT Record: SPF records are published as TXT records in your domain’s DNS settings.
- IP Addresses: The record contains a list of allowed IP addresses.
- v=spf1: All SPF records start with this tag.
- Include Mechanism: Allows you to include SPF records from other domains (e.g., your email service provider).
- ~all (SoftFail) vs. -all (HardFail): These define the policy for emails from unauthorized sources. ~all suggests a soft approach, while -all is stricter, often leading to rejection.
Check our free SPF checker tool now!
DomainKeys Identified Mail (DKIM): Is the Email Untouched?
DKIM adds a digital signature to your outgoing emails, acting like a tamper-proof seal. This signature allows the receiving server to verify that the email hasn’t been altered in transit and that it genuinely originated from the claimed sender’s domain.
How DKIM Works
- Sender’s Signing: The sending mail server uses a private cryptographic key to generate a unique digital signature for each outgoing email. This signature is placed in the email’s header.
- Public Key Publication: The domain owner publishes a corresponding public key in their DNS as a TXT record.
- Receiver’s Verification: When the receiving server gets the email, it uses the public key (retrieved from DNS) to decrypt the signature.
- Integrity Check: If the decrypted signature matches the email’s content and header information, it confirms that the email hasn’t been changed since it was signed and that it came from the rightful sender.
Key Aspects of DKIM
- Cryptographic Keys: DKIM relies on a pair of keys: a private key (kept secret by the sender) and a public key (published in DNS).
- Digital Signature: This signature is embedded in the email header.
- Content Integrity: Ensures that the email’s subject, body, and attachments remain unchanged.
- Domain Ownership: Verifies that the email originates from the domain that claims to be sending it.
Domain-based Message Authentication, Reporting, and Conformance (DMARC): The Policy Enforcer
DMARC builds upon SPF and DKIM, acting as a policy layer that tells receiving mail servers what to do if an email fails SPF or DKIM authentication. It also provides a feedback loop, sending reports back to the sender about authentication failures. This allows domain owners to monitor and improve their email sending practices.
How DMARC Works
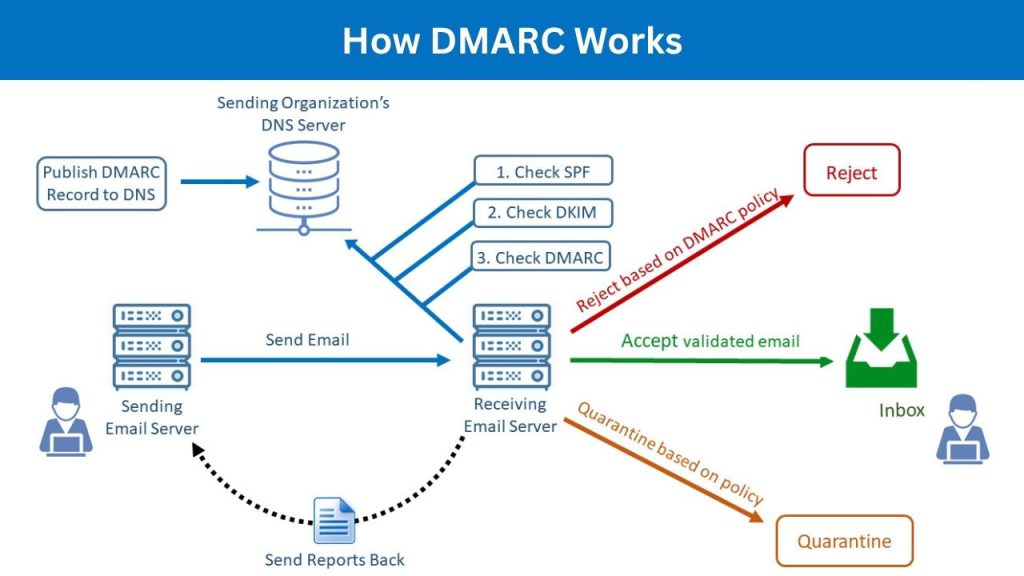
- Policy Publication: The domain owner publishes a DMARC policy as a TXT record in their DNS. This policy specifies:
- What to do if an email fails SPF and/or DKIM (e.g., p=none, p=quarantine, p=reject).
- Where to send aggregate and forensic reports about authentication failures.
- Alignment Check: DMARC requires “alignment.” This means the “From” domain shown to the user must match the domain verified by SPF or DKIM. Without alignment, even if SPF or DKIM pass, DMARC can still fail.
- Receiver’s Action: The receiving server checks both SPF and DKIM. If either passes and aligns with the “From” domain, DMARC passes. If both fail or don’t align, the server applies the policy defined in the DMARC record.
- Reporting: DMARC generates reports (aggregate and forensic) that provide insights into email authentication results, helping domain owners identify legitimate emails that are failing and malicious attempts to spoof their domain.
Key Aspects of DMARC
- Policy Enforcement: Defines actions for failed authentication (none, quarantine, reject).
- Reporting: Provides valuable data on email authentication performance and potential abuse.
- Alignment: Crucial for DMARC to pass, ensuring the visible “From” address matches the authenticated domain.
- Gradual Implementation: It’s best to start with p=none to monitor results, then gradually move to p=quarantine and p=reject as you gain confidence.
How SPF, DKIM, and DMARC Relate to Email Verification
While SPF, DKIM, and DMARC are authentication protocols, they are intrinsically linked to the broader concept of email verification and deliverability.
- Sender Reputation: Passing these checks boosts your sender reputation. A good reputation means your emails are trusted by receiving servers.
- Reduced Bounce Rates: When your emails are properly authenticated, fewer will be rejected as spam or phishing attempts, leading to lower bounce rates.
- Improved Inbox Placement: Emails from authenticated domains are far more likely to land in the recipient’s inbox, rather than their spam or junk folder.
- Preventing Impersonation: These protocols actively prevent others from sending emails using your domain without your permission, safeguarding your brand.
- Data Accuracy and Cleanliness: By ensuring your outbound emails are correctly verified and delivered, you implicitly rely on the accuracy of the recipient email addresses. Sending to invalid or risky addresses can negatively impact your sender reputation, even with a perfect SPF/DKIM/DMARC setup.
Enhancing Your Email Marketing Strategy with MyEmailVerifier

Properly configuring SPF, DKIM, and DMARC is crucial, but it’s only one piece of the puzzle for successful email marketing. Even with perfect authentication, sending emails to outdated, invalid, or risky addresses can harm your sender reputation and lead to poor deliverability. This is where a robust email verification service like MyEmailVerifier becomes invaluable.
MyEmailVerifier helps you maintain a clean and healthy email list by:
- Identifying Invalid Emails: Removing addresses that are no longer active, improving your bounce rate.
- Detecting Spam Traps: Identifying email addresses that can severely damage your sender reputation.
- Spotting Disposable Emails: Filtering out temporary email addresses that offer no long-term value.
- Catch-All Detection: Helping you understand which addresses might accept all mail, regardless of validity.
By proactively cleaning your email lists with MyEmailVerifier, you ensure that your authenticated emails reach genuine recipients, maximizing your campaign effectiveness and protecting your hard-earned sender reputation. It complements your SPF, DKIM, and DMARC efforts by ensuring the “who” you send to is as reliable as the “how” you send.
Best Practices for Implementing SPF, DKIM, and DMARC
Setting up these protocols correctly is vital. Here are some best practices:
- Start with SPF: Ensure all legitimate sending IP addresses for your domain are included. Be mindful of the 10 DNS lookup limit for SPF records.
- Implement DKIM for all Outgoing Mail: Make sure all your email-sending services (e.g., marketing platforms, transactional email providers) are signing your emails with DKIM. Use 2048-bit key lengths for better security and rotate keys regularly.
- Gradually Deploy DMARC: Begin with a p=none policy to monitor reports and identify any legitimate mail failing authentication. Once confident, move to quarantine and eventually reject.
- Monitor DMARC Reports: Regularly analyze the aggregate and forensic reports to understand your email ecosystem, identify spoofing attempts, and troubleshoot authentication failures.
- Maintain DNS Records: Keep your SPF, DKIM, and DMARC DNS records updated as your email infrastructure changes.
- Secure Parked Domains: Even domains not actively sending emails should have SPF and DMARC records to prevent spoofing.
Conclusion
SPF, DKIM, and DMARC are not optional extras; they are fundamental components of modern email security and deliverability. They work in concert to build trust in your email communications, protect your brand from malicious actors, and ensure your messages consistently reach their intended audience. By understanding and correctly implementing these protocols, you lay a strong foundation for successful email marketing and communication. Pair these efforts with robust email list hygiene, as offered by services like MyEmailVerifier, and you’re well on your way to email success.
Ready to improve your email marketing? Try MyEmailVerifier today.
FAQ Section
What is the main difference between SPF, DKIM, and DMARC?
SPF identifies authorized sending servers, and DKIM verifies that an email hasn’t been altered and came from the claimed domain via a digital signature. DMARC sets a policy for what to do when SPF or DKIM fail, and provides reporting on those failures.
Do I need all three (SPF, DKIM, and DMARC) for email authentication?
While SPF and DKIM can function independently, DMARC truly maximizes their effectiveness by providing policy enforcement and reporting. Implementing all three is highly recommended for robust email security and deliverability.
How do I set up SPF, DKIM, and DMARC for my domain?
You set up SPF, DKIM, and DMARC by creating specific DNS TXT records in your domain’s DNS settings. The exact steps vary slightly depending on your domain registrar and email service provider, but generally involve adding these records to your domain’s DNS zone.
What happens if an email fails SPF, DKIM, or DMARC checks?
If an email fails these checks, the receiving server’s action depends on the DMARC policy set by the sender’s domain. It could be delivered (if p=none), sent to spam/junk (if p=quarantine), or completely rejected (if p=reject). Without DMARC, the action is up to the receiving server’s discretion.
Can SPF, DKIM, and DMARC prevent all email spoofing?
While SPF, DKIM, and DMARC significantly reduce email spoofing and phishing, no single solution is 100% foolproof. When properly configured, these powerful tools make it far more difficult for malicious actors to impersonate your domain.

James P. is Digital Marketing Executive at MyEmailVerifier. He is an expert in Content Writing, Inbound marketing, and lead generation. James’s passion for learning about people led her to a career in marketing and social media, with an emphasis on his content creation.